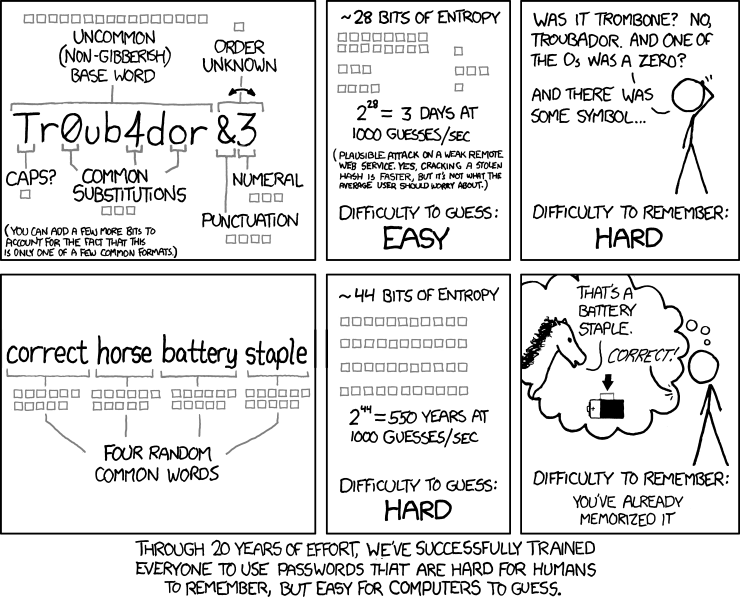
 Why is it that I never have trouble remembering that XKCD comic? I even recall the passphrase has 44 bits of entropy! My network password with at least two special characters, a capital letter, and a number is a different story. I have that written down for safe keeping. This scenario sums up the problem with passwords: “hard for humans to remember, but easy for computers to guess.”
Why is it that I never have trouble remembering that XKCD comic? I even recall the passphrase has 44 bits of entropy! My network password with at least two special characters, a capital letter, and a number is a different story. I have that written down for safe keeping. This scenario sums up the problem with passwords: “hard for humans to remember, but easy for computers to guess.”
How do weak passwords form a singular failure point in cryptography? They don’t, they form many. Too many failure points to list.
Passwords protect cryptography and are everywhere. Private keys, administrative accounts, Zip files – all encrypted with passwords. In many ways, passwords are the weakest link in cryptography because they are directly controlled by the human operator.
Password weaknesses fall into two major categories:
- Directly impacting cryptographic strength; and
- Protecting assets that hold cryptographic access.
Encrypted drives are an example of the former, while a storage account for the private key of an enterprise certificate authority is an example of the latter. No matter how strong the cryptographic technology is, if it is held in a poorly protected account the cryptography is no stronger than the weakest password.
Although cryptographic keys and certificates are occasionally rotated or refreshed, it is common practice to keep older private keys kicking around. “What’s the harm, we’re no longer using that key” is often the rationale given, but this leaves you vulnerable to a harvesting attack. Imagine an adversary can capture network traffic or stored files that are encrypted with this key. Although the key may not be compromised today, a later compromise of an account that holds this key — even if it is expired/rotated — can now be used to decrypt the data that was captured in the past.
Cryptographic policy management ensures that cryptographic algorithms, key lengths, entropy requirements, rotation schedules, and key routing is set through a policy that is applied at all cryptography points.
Too often, this concept of creating a policy at the CIO level for cryptography ends right there. Instead, it should carry forward to passwords. Not a minimum password strength policy — this is not sufficient. If cryptographic access is at any point protected by a password, its strength and minimum requirements MUST, at a minimum, meet the requirements of the cryptographic assets that your policy controls. Remember, what is your weakest link?
I recognize that many key-based, biometric-based, and two-factor type technologies are replacing traditional passwords, however, the concepts discussed earlier carry on. These technologies simply extend the cryptographic chain to a device, or an API, or even tokens stored in the cloud. If your strong, cryptographically diverse, and out-of-band cryptography system can be accessed by the compromise of a single cloud-stored biometric token, the weakest point in the cryptographic link is not with the cryptographic system — it is with the password protecting it.
Don’t miss the other Single Points of Failure in Cryptography posts by Vince Berk, Chief Strategy Officer: Public Handshake, Asymmetric Encryption and Weak Entropy.


