Defending Encryption: Quantum XChange at Cisco Live Amsterdam

Back to Blogs & Podcasts
21 Nov 2025
In today’s rapidly evolving digital landscape, two transformative technologies—: quantum computing and artificial intelligence— are reshaping cybersecurity. The AI Networking Summit had discussions on quantum and AI.
These two distinct but complementary technologies are converging to solve complex problems. Quantum AI could use quantum computing to enhance machine learning and create more powerful AI models to positively impact drug discovery and research for the medical and pharmaceutical industries.
Both quantum and AI promise new breakthrough capabilities, but they also introduce significant risks that organizations must urgently address.
While quantum computing and AI differ in their technical foundations, they share striking similarities in how they challenge traditional cybersecurity:
AI enables faster, more adaptive cyberattacks: —automating reconnaissance, exploiting vulnerabilities, and evading detection. Quantum computing has the power to break today’s encryption standards, eliminating data privacy and confidentiality.
Together, they are a deadly combination. Because of the power of quantum computing, it can be used to optimize existing AI-driven malware attacks, analyze vulnerabilities to discover new ways to access data and accelerate zero-days identification, and develop improved AI-driven social engineering models.
AI can convincingly spoof identities, generate deepfakes, and manipulate data integrity. Quantum computing undermines the cryptography that serves as the foundation of trust in digital communications.
Both technologies favor attackers. AI tools are widely available and easy to weaponize. Quantum capabilities can be leveraged by nation-states and elite adversaries—creating a dangerous imbalance in cyber defense.
Harvest now, decrypt later (HNDL) attacks are happening today. Adversaries are collecting encrypted data today to decrypt with quantum computers. Similarly, AI-driven attacks are happening in real time, exploiting gaps in detection and response.
Quantum computing can perform complex tasks that today’s classical computers cannot; the ability to efficiently break widely used cryptographic algorithms. Even post-quantum cryptography (PQC) algorithms, while promising, are not a silver bullet. They are also vulnerable to being broken, so organizations must plan to change algorithms as needed for data security and confidentiality.
With the speed of AI-generated attacks and the power of quantum computing, encryption updates will become part of standard IT planning. Keeping the same algorithms in use for more than 40 years is no longer a reality.
NIST released four PQC algorithms in 2024, with more under evaluation since the likelihood is that they will eventually be broken, and regular updates will be required to maintain data security.
You need more than an algorithm; you need an architecture.
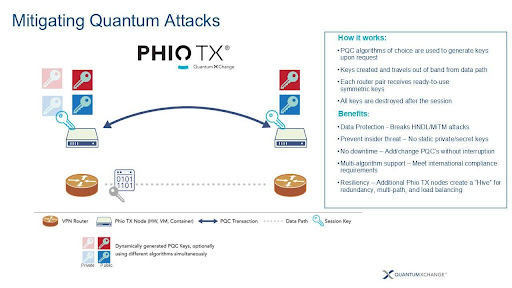
Phio TX’s secure-by-design architecture addresses the dual threats of quantum and AI to safeguard sensitive communications, classified data, and critical infrastructure from next-generation threats. It’s a practical and resilient solution that strengthens today’s encryption and enables the seamless implementation of PQC’s.
Protect your largest attack surface, the network, against AI-enabled quantum attacks with these capabilities:
Harden your existing infrastructure. Rapidly deploy NIST and other PQCs globally; set up a POV in hours, then quickly scale as needed.
Industry’s first FIPS 203 and FIPS 140-3 validated solution. Independent, third-party assurance of compliance with rigorous U.S. government security standards.
Keys are never reused and never stored, reducing the attack surface and neutralizing AI-driven pattern recognition or replay attacks. NIST Entropy Source Validation (NIST SP 800-90B) ensures keys are truly unpredictable.
Phio TX separates key delivery from data transmission, eliminating the risk of key interception, protecting against Harvest Now Decrypt Later (HNDL), and quantum attacks.
Ensure that AI models, training data, and inference pipelines are protected from eavesdropping and data theft.
Quantum and AI are not distant threats; —they’re converging realities. Both have strategic implications for government and industry. The public and private sectors must act now to secure their data and communications.
Phio TX helps enforce strong encryption practices to stay ahead of evolving threats, advances in computing, and everyday cybersecurity risks to your data. Narrow your largest attack surface against quantum attacks by protecting your network in a FIPS-validated, easy-to-deploy way.
To learn more, watch our AI Networking Summit 2025 session: https://onug.net/events/post-quantum-cryptography-made-easy-quantum-xchange-triple-t/
Have one of our experts show you how Phio TX protects your organization from threats today and the quantum future.
Request Request
a a
demo demo
