Manage encryption continuously, holistically, and through policy with CipherInsights.
80%
of traffic on the network has some defeatable flaw in its encryption.
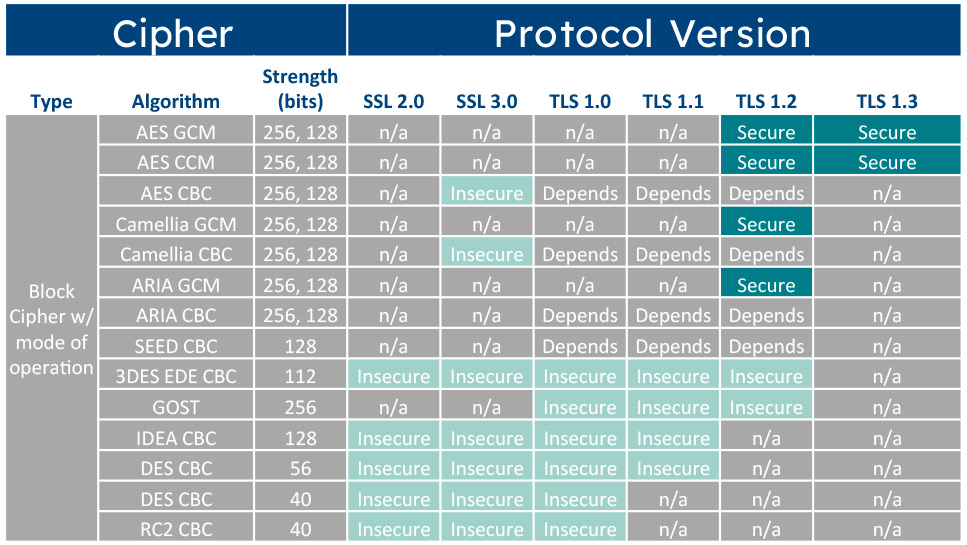
At one point in time, “insecure” was “secure.” Networks have “soft chewy centers” – firewalls may protect the perimeter, but many communications are unencrypted, certificates are weak, and very old and defeated standards such as MD5, SHA-1, TLS 1.1, or SSL 3.0 are still being used.
Combat cyber risk and kick-start your inevitable migration to quantum-safe cryptography.
CipherInsights is a passive listener on the network, capable of identifying dozens of cryptographic risk factors in real time.
- Encrypted vs. unencrypted traffic
- Quantum-vulnerable cryptography in use
- Third-party risk
- Client, server, and IoT inventory
- Database creation and access
- Signed or self-signed certs
- Expired certificates
- Certification validation to CA
- Authentication validation
The sensor-based tool and on-the-wire analysis differs from network visibility and vulnerability scanners in that it scans and analyzes all traffic – even outbound traffic destined for an external host. Because CipherInsights is not limited to analyzing endpoints on the LAN, it can see how encryption is working vs. how it was designed to work – bringing visibility to network security blind spots.
See it in Action
Certificate Chain Analysis
On-the-Wire Analysis
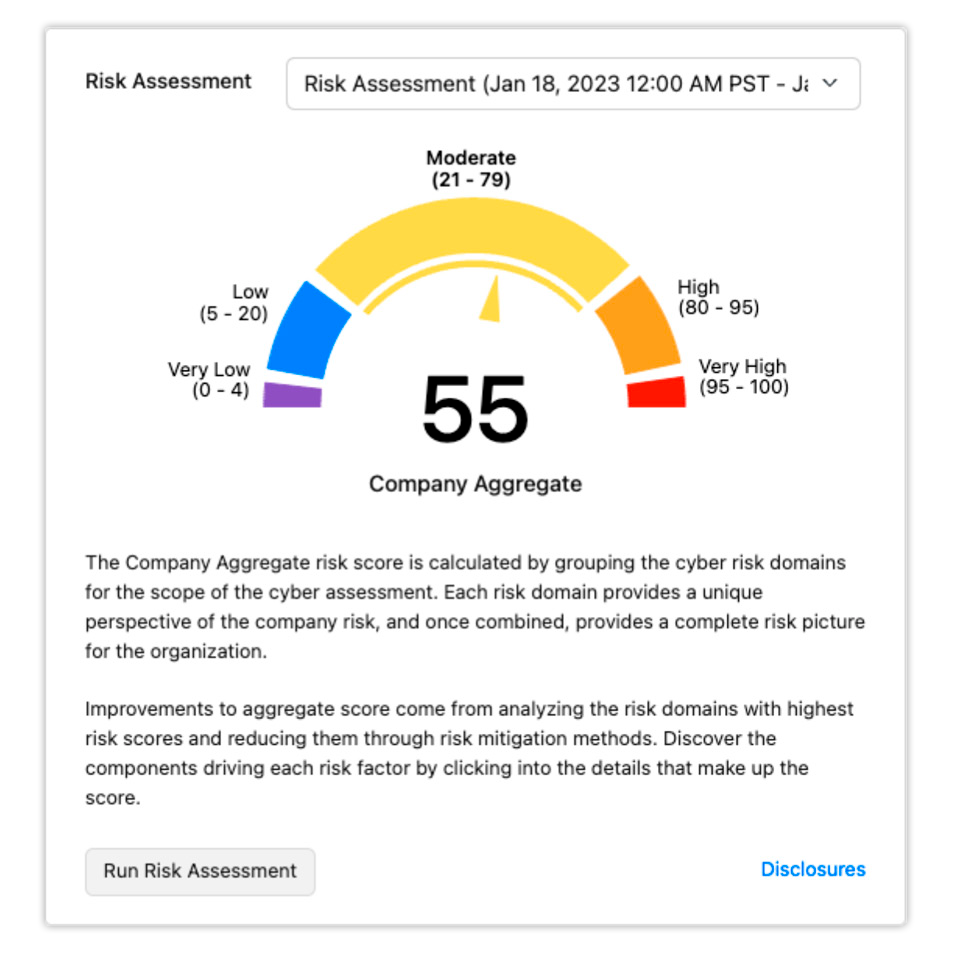
Dashboard Reporting
Monitor and manage organizational progress toward a fully diversified, quantum-safe, and crypto-agile network.
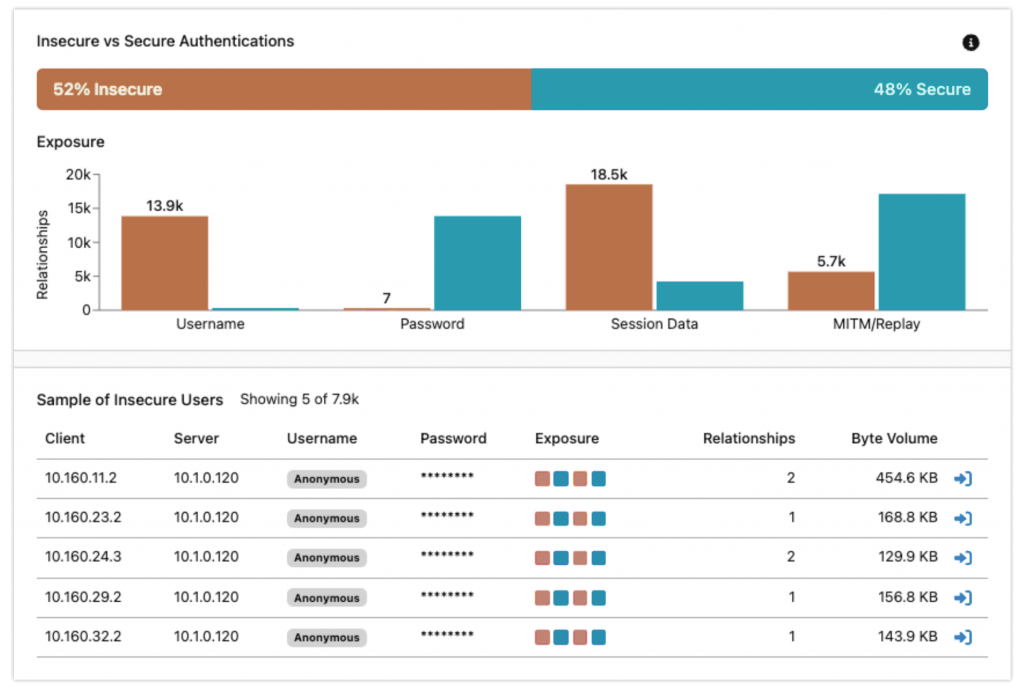
Continuous risk assessment by CipherInsights enables users to prioritize mitigation, maintain compliance, enforce policies, better protect critical data, and improve overall security posture.
PCI-DSS 4.0 Countdown Begins
Version 4.0 of the Payment Card Industry Data Security Standard includes new enterprise encryption requirements including an annual inventory of cryptography used by in-scope systems. Quantum Xchange can help.
Download the Solution Brief


