Once purchased by large enterprises only, cyber insurance is now a priority for companies of all sizes as they look to reduce the financial losses resulting from a security breach while reassuring board members, stakeholders, and investors.
Learn how CipherInsights from Quantum Xchange can help secure a premium through continuous monitoring and assessment of cybersecurity risk on the network.
With the cost of a data breach rising year-over-year, the attack surface continuing to expand, and ransomware showing no signs of slowing down, cyber insurance can provide the critical support needed to cover payments for legal services, investigations, and remediation.
Once purchased by large enterprises only, cyber insurance is now a priority for companies of all sizes as they look to reduce the financial losses resulting from a security breach while reassuring board members, stakeholders, and investors. As a result, experts predict the cyber insurance market will double from $15 billion to more than $30 billion over the next five years and could reach $100 billion by 2030.
Comprehensive cyber risk governance has become a prerequisite for coverage. With 28% of cyber claims denied, organizations must demonstrate they can accurately identify, assess, mitigate, and monitor cybersecurity risk to secure a premium.
Automated Cyber Insurance Compliance
CipherInsights from Quantum Xchange can monitor and assess cybersecurity risk on the network and measure compliance against cyber insurance mandates. The real-time visibility product continuously monitors network traffic measuring and scoring compliance with the security criteria mandated by most cyber insurance companies, including:
- Multifactor authentication
- Patch management and vulnerability scanning
- Endpoint detection and response
- Cybersecurity awareness training
- Identity management
- Network segmentation
- Backup protection
- Breach plan/incident response plan
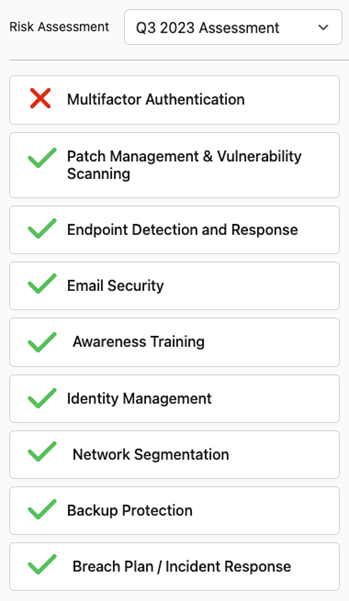
The powerful assessment tool provides users with a quick understanding of how data is accessed in their environment, what security policies are truly being implemented, and a prioritized checklist of what needs to be remediated to ensure compliance.
Uncover missing mandates before your claim is denied.
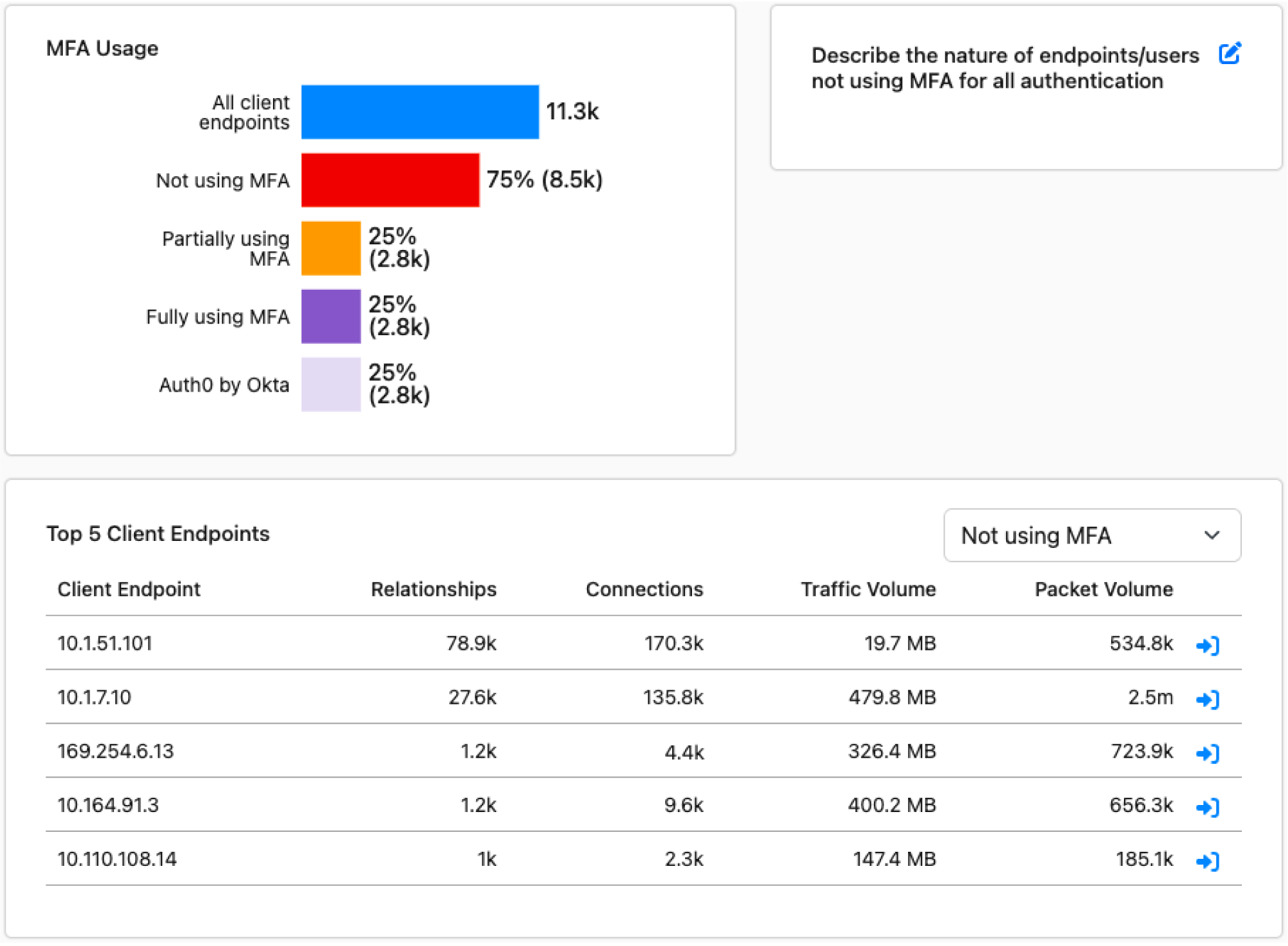
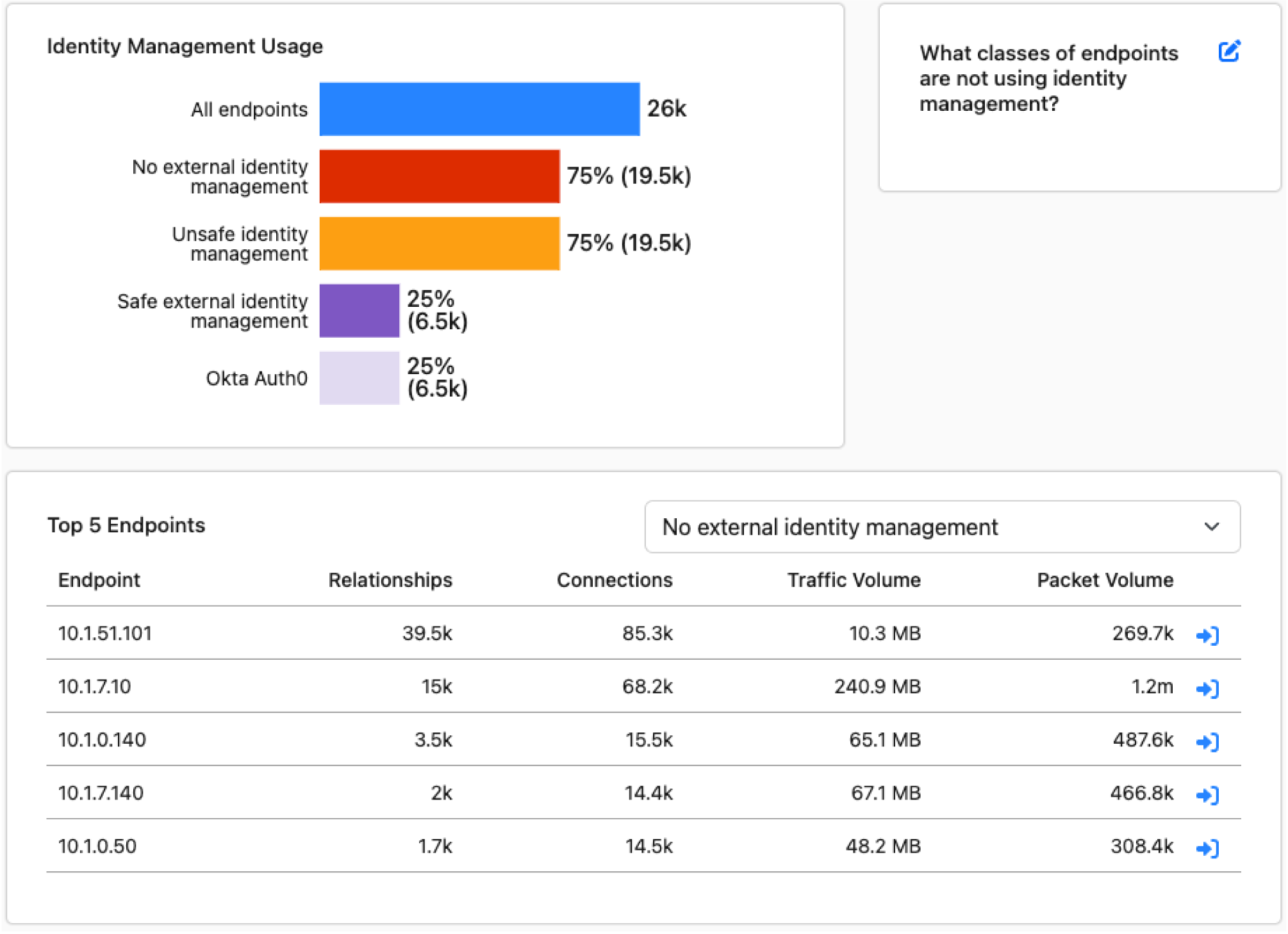
Once resolved, organizations can maintain security policy enforcement through continuous monitoring, customized policy alerts, and board-level dashboards that provide a factual, up-to-date view of what’s happening on the network at any given time.
Ensure the proper deployment and operation of your cyber controls.
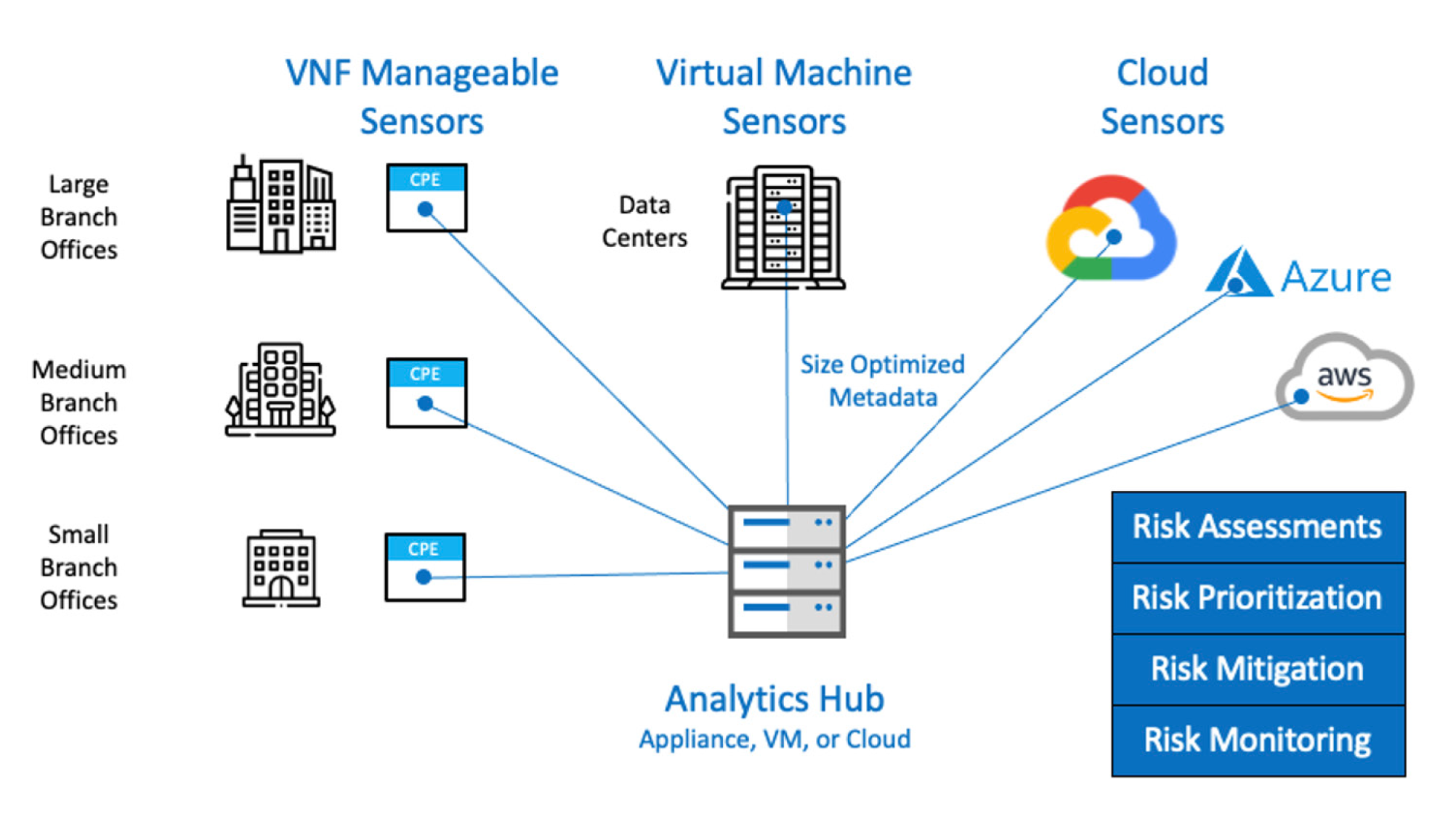
Requirements and Deployment
Deployed as a passive listener on the network, CipherInsights is delivered as a virtual appliance which connects to a packet broker or SPAN/TAP. The non-intrusive solution offers unparalleled network visibility unavailable by other scanning technologies. IP and port agnostic, CipherInsights analyzes conversations anywhere on the network, from all directions — north-south and east-west. Its deep decoding capabilities identify all aspects of network sessions: IP, port, DNS name, protocol, encryption type, and certificate details including the entire trust chain.
Sensor-Based Monitoring
With CipherInsights you can:
- Ensure accurate and up-to-date data is used in cyber insurance applications.
- Maintain compliance with cyber insurance mandates as computing infrastructure evolves.
- Secure premiums based on real cyber-risk data.
- Mitigate risk due to ineffectively implemented security controls.
- Continuous monitoring to ensure risk is kept in lockstep with the business as it evolves.

Contact us today to learn more at info@quantumxc.com

