Most professionals in the security industry understand the pains, challenges, and time it takes to complete a cryptographic transition. It took more than 20 years for the Advanced Encryption Standard (AES) to completely replace Data Encryption Standard (DES) and 3DES. If you haven’t heard the noise, a quantum computer will be able to break RSA-2048, considered the gold standard for Public Key Encryption (PKE), the system that has for years protected our digital universe.
In 2016 the National Institute for Standards and Technology (NIST) warned that all organizations start preparing then for the coming quantum-crypto break. Unfortunately, most have made very little, if any, movement to heed this advice. Our partners at Thales released an industry survey that found 72% of organizations see quantum computing affecting them in the next five years. However, in a similar survey conducted by DigiCert only 56% of organizations surveyed were learning quantum-safe practices.
Unlike Y2K, when there was a definitive deadline and end-date to work against, Y2Q is ambiguous causing too many companies to take a lackadaisical, wait and see attitude to quantum preparedness planning and execution. Many are waiting for the Post-Quantum Cryptography (PQC) selection process by NIST to yield the final standard before they take action.
This is flawed, shortsighted thinking. Consider the following:
- A quantum computer may be available before the final PQC selection process is finalized and the full transition is completed. Google CEO Sundar Pichai at Davos 2020 said he expects that quantum computing will break encryption as we know it in the next 5-10 years.
- There is no guarantee that the cryptographic standards selected will not be broken by adversaries or vulnerable to implementation errors. Some even argue a quantum attack by a nation-state could occur without anyone’s knowledge. Roger Grimes, author of the book Cryptography Apocalypse goes a step further to announce, “I predict that someone will publicly announce that they have used a quantum computer to break a traditional asymmetric key cipher. It’s been the Holy Grail since 1994 and I predict it happens next year.”
- Harvest today, decrypt tomorrow attacks are happening now.
- Current PKE systems, i.e., TLS/SSL and key management practices are rife with vulnerabilities putting today’s data and communications networks at risk. With PKE, the encryption keys and data travel together. An attacker needs only to compromise one connection to obtain secret information.
Last week, NIST published the final version of its report titled, Getting Ready for Post-Quantum Cryptography outlining the challenges associated with adopting and using PQC algorithms after the standardization process is complete — which is currently on pace for selection by 2022-24. NIST also cautions that in the best case, another 5-15 more years will be needed after the publication of the cryptographic standards before a full transition is completed.
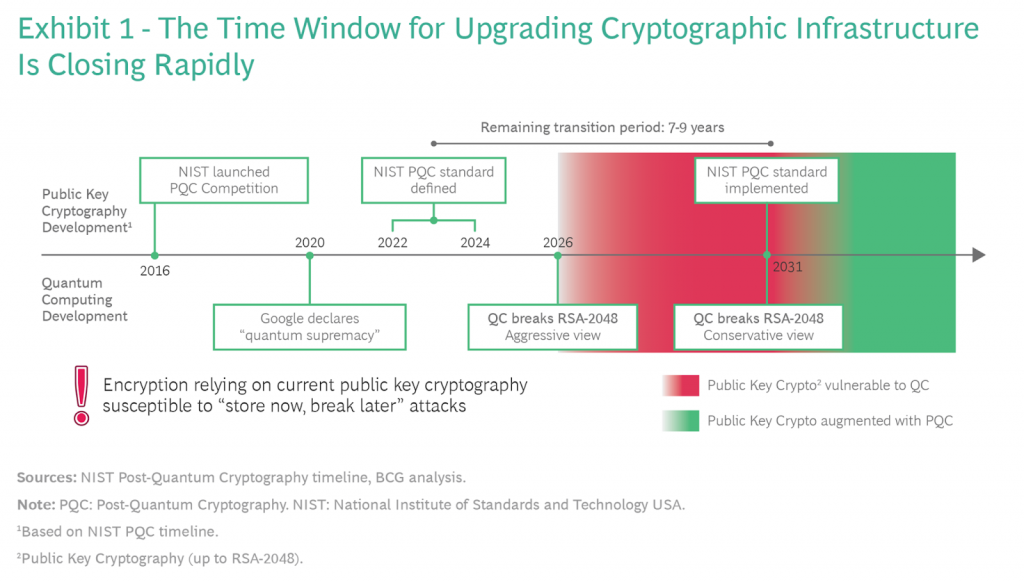
Boston Consulting Group (BCG), in its March 30, 2021 article, “Ensuring Online Security in a Quantum Future” (see our take on this informative, must-read article here) published the below timeline in response to the NIST PQC project and warned, “This implies that window for upgrading existing infrastructure is seven to nine years — too short for such an ambitious goal.” In concluding, “companies in all industries need to take note now and plan for encryption in the quantum future now.”
Quantum Xchange understands the challenges and complexities of cryptographic transitions can be overwhelming, if not paralyzing. We’ve built a practical and highly scalable, quantum-safe key distribution system that allows organizations to get started now with very little lift or outlay. In fact, our affordable, crypto-agile path to quantum safety can be easily dropped into organizations’ existing crypto infrastructure today.
Phio Trusted Xchange (TX) is a simple architecture overlay that leverages a patent-pending out-of-band symmetric key delivery technology to supplement native encryption with an additional key-encrypting-key (KEK) transmitted independently of the data path. The system supports quantum keys from any source i.e., PQC (all candidate KEM algorithms), QKD, QRNG, or combination. Organizations can easily increase quantum protection levels based on their data inventory requirements and risk tolerance levels without any disruption to the network. Learn more here.
See how Phio TX addresses all of the foreseeable challenges of PQC adoption outlined by NIST in the solutions brief, “A Response to NIST’s Post-Quantum Cryptography Adoption Challenges and Planning Requirements” available here.
Don’t be left behind and vulnerable. Let us show you how we can protect you today.
See Phio TX in Action


