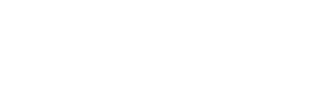Phio TX hardens your existing infrastructure against quantum threats and ensures a seamless transition to post-quantum cryptography (PQC). Operate with confidence, knowing your data is secure today against the quantum attacks of tomorrow.
Flexible Architecture

Rapidly deploy PQC’s at scale. Easily switch between technologies (PQC, QKD, QRNG) on the fly.

Available in multiple form factors – container, software, secure hardware. Supports cloud, hybrid, on-premises deployments.

Quickly set up a POV in a few hours. Start small with simple P2P setup then seamlessly scale to thousands of nodes.

Supports SKIP, ETSI for drop-in integration with no router config changes.
Stronger Data Security Today
Phio TX breaks the crypto monoculture that exists today to provide a resilient, crypto-agile, and crypto-diverse management system for the ages. It enables a crypto center of excellence (CCoE) and gives CIOs a policy management and monitoring platform to deploy, validate, and configure traditional and post-quantum cryptographic algorithms.
Features
• Graphical User Interface (GUI) view of the routing and transmission of quantum safe keys throughout the enterprise
• Easily integrates with existing networking and security products to make them quantum safe
• Continuous key rotation, multipath, intelligent key routing maintain confidentiality and integrity of sensitive data
• Failed algorithms no longer a threat, easily switch PQC’s, keys, algorithms on the fly
Form Factors
Phio TX is available in a variety of deployment options to meet all budgetary and business requirements. Pricing is based on a software-as-a-service licensing model and is dependent on the number of nodes and clients supported per month.


- An architectural, patent-pending, solution that enables out-of-band quantum security
- Provides crypto-agility & defense-in-depth, Phio TX can incorporate QKD, PQC, QRNG
- Targeted for enterprises & governments


- Virtualized container application with Cisco® networking native integration
- Most secure SKIP PQC implementation available. Requests kept within Cisco device crypto boundary.
- Over-the-network management of Phio TX as an integrated process within the network itself.


- Edge device for branch offices, remote installations, SMB and work-from-home markets
- Easy to deploy, cost-effective ”on-ramp” to Phio TX networks

- Leverages cloud to efficiently facilitate out-of-band key delivery
- Creates mesh network where continuous key rotation and multi-path key routing occur
- Provides simple/effective means to scale Phio TX networks & provide bespoke customer solutions


- Quantum-safe and AI-native VPN for modern networking
- Two-tunnel solution where dynamically keyed VPN tunnels can be either outer or inner
- Key exchange and user authentication is separate from data path
- Site-to-Site supports cloud and legacy network hardware and is best suited for stationary deployments
- Remote Access allows thousands of mobile-clients to establish individual secure VPN tunnel to the office network
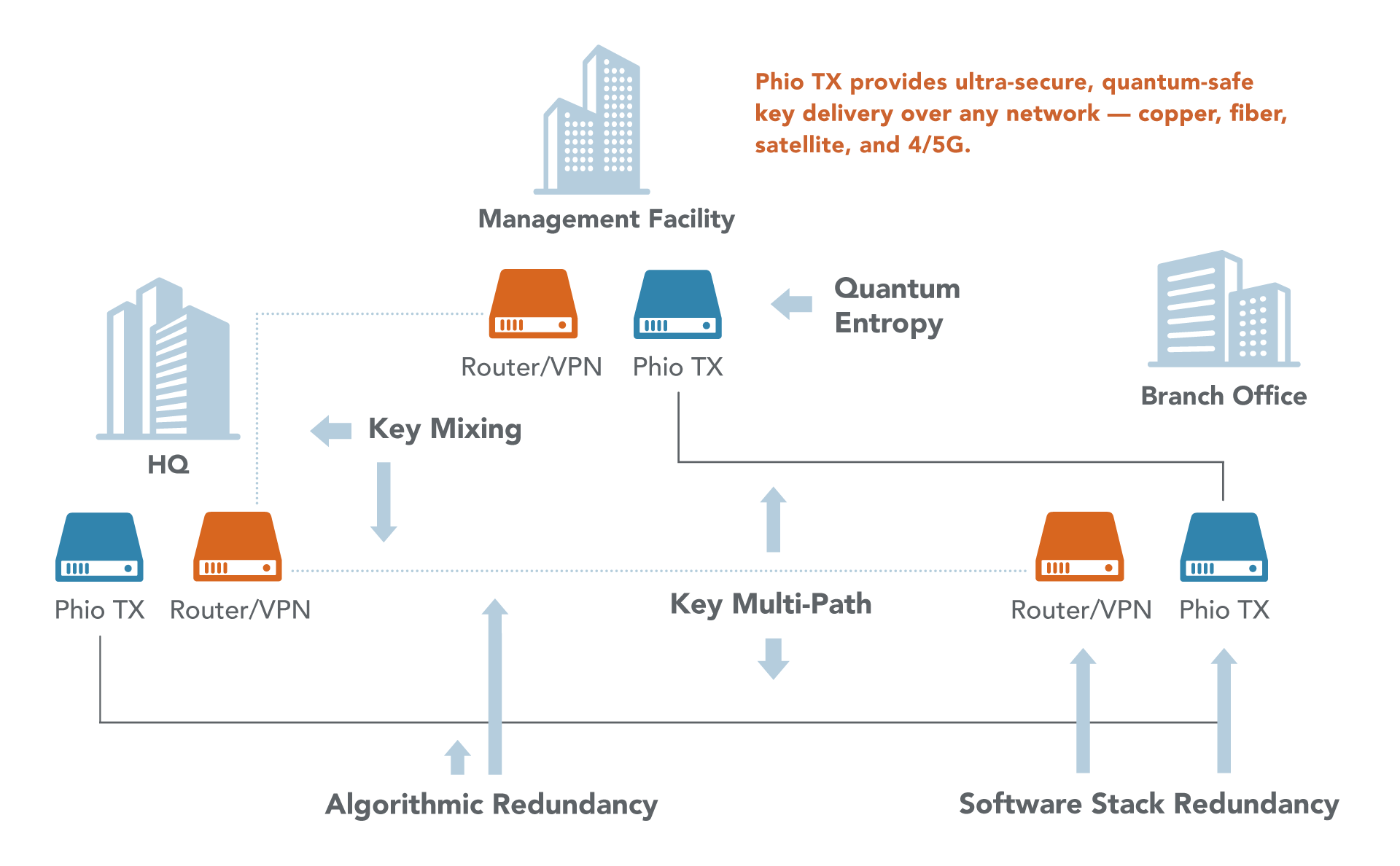
Phio TX leverages five important aspects essential to next generation cryptographic security:

Redundant out-of-band key delivery

Quantum entropy

A diversified collection of current and postquantum algorithms

Software stack redundancy

Key mixing
It works with an organization’s existing encryption and network environment and a quantum-key source (QRNG, PQC, QKD) to send a second, symmetric key out-of-band down a quantum-protected tunnel and mesh network independent of the data path.
Don’t fall victim to any one bug, flaw, leaked certificate, or PQC algorithm. Dynamically, stack, switch, mix, and deliver quantum-safe keys across any network media type, anywhere on the planet, with no network interruptions or downtime.
An attacker must now know that multiple independent encryption implementations and algorithms are present, with two keys in play — when, where, how, or if they are paired, and what cryptographic algorithm they are paired with.
The added complexity and randomness brought by this crypto-diverse network significantly reduces the risk in, or damage of, a would-be attack because session keys, PQCs, certificates, etc., are continuously changing. Further, Phio TX removes single points of failure common to modern-day encryption practices by taking a proactive, capricious approach to key delivery. Organizations won’t always know which part of a crypto stack has been defeated and how, but it won’t matter if the cryptography is sufficiently diversified.