Post-Quantum Cryptography in 2026: What Infrastructure Leaders Need to Know

Purpose-built key management that neutralizes Harvest Now, Decrypt Later (HNDL) attacks today and adapts as cryptography evolves—without downtime, performance impact, or infrastructure overhaul.
See See
Phio Phio
TX TX
in in
Action Action
Trusted by industry leaders































Hot-swap cryptographic methods with zero downtime through centralized policy control.
Seamless integration with existing network architecture—operational in days, scalable to enterprise-wide deployment.
Out-of-band key management that removes the single point of cryptographic failure.
As NIST evaluates 45+ additional algorithms, Phio TX adopts new standards quickly without application rewrites. Built for multiple rounds of PQC evolution.


Phio TX overlays existing SKIP and ETSI supported infrastructure to enable quantum-safe networking seamlessly.
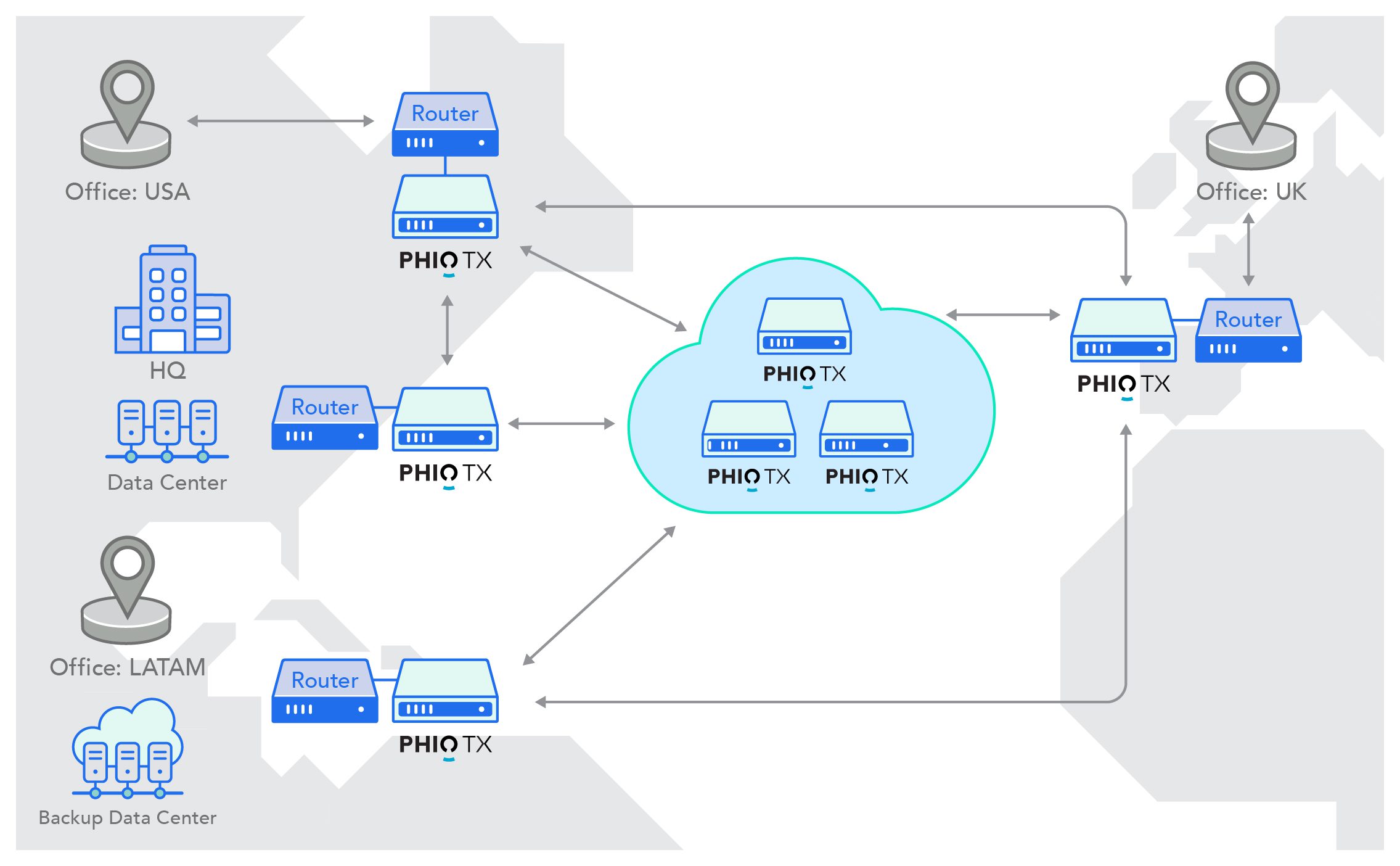
Virtual container allows you to provision, install, and configure over-the-network as an integrated process within your existing infrastructure.
learn learn
more more
Deploy on AWS, Azure, and Google Cloud Platform (GCP) to quickly scale across the enterprise.
Learn Learn
more more
Datacenter-ready appliance works seamlessly across hybrid environments fully integrating with cloud and container deployments.
Learn Learn
more more
view view
all all
resources resources
Every day of delay is another day of vulnerability. The technology is ready, and the threat is real. See how Phio TX can protect your critical, data-in-motion today and in the post-quantum world.
Request Request
a a
demo demo
